What Is The OSI Model
The OSI model describes seven layers that computer systems use to communicate over a network. It was the first standard model for network communications, and it was adopted in the early 1980s by all major computer and telecommunications companies.
The modern Internet is based on the simpler TCP/IP model rather than the more complex OSI model. However, the OSI 7-layer model is still widely used because it makes networking issues easier to identify and resolve by helping to communicate and visualize how networks function.
The OSI model was introduced in 1983 by representatives of major computer and telecommunications companies and was adopted as an international standard by 1984.
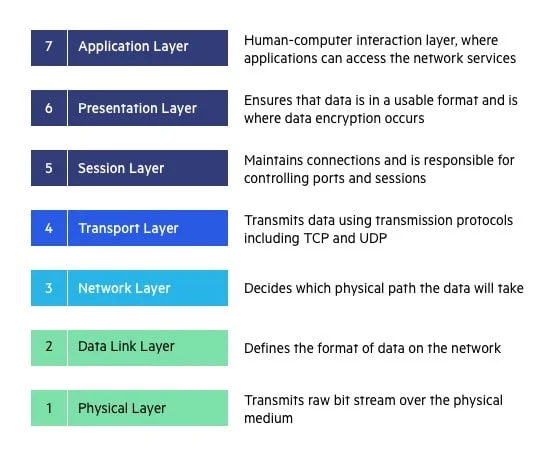
The 7 Layers
Here are the OSI layers described from the application layer down to the physical layer:
7. Application Layer
End-user software such as web browsers and email clients use the application layer. It defines protocols that allow software to send and receive data and present meaningful information to users. The Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), Post Office Protocol (POP), Simple Mail Transfer Protocol (SMTP), and Domain Name System are all examples of application layer protocols (DNS).
6. Presentation Layer
Data is prepared for the application layer by the presentation layer. It specifies how two devices should encode, encrypt, and compress data in order for it to be properly received on the other end. Any data transmitted by the application layer is prepared for transmission over the session layer by the presentation layer.
5. Session Layer
The session layer establishes communication channels between devices, known as sessions. It is in charge of starting sessions, keeping them open and functional while data is transferred, and closing them when communication ends. Additionally, the session layer has the ability to set checkpoints in the middle of a data transfer, allowing devices to pick up where they left off in the event of a session interruption.
4. Transport Layer
Data transferred in the session layer is divided into “segments” by the transport layer at the receiving end. On the receiving end, it is in charge of putting the segments back together in order to create data that the session layer may use. The transport layer performs error control, which determines whether data was received wrongly and, if not, requests it again, as well as flow control, which sends data at a pace that matches the connection speed of the receiving device.
3. Network Layer
The network layer serves two primary purposes. One is dividing segments into network packets, which are then put back together at the other end. The alternative method of packet routing involves finding the optimum route through a physical network. In order to route packets to a destination node, the network layer needs network addresses, which are commonly Internet Protocol addresses.
2. Data Link Layer
The data link layer creates and breaks connections between two network nodes that are physically close to one another. It splits up packets into frames and sends them from source to destination. This layer is made up of two components: Media Access Control (MAC), which utilizes MAC addresses to connect devices and specifies permissions to transmit and receive data, and Logic Link Control (LLC), which identifies network protocols, does error checking, and synchronizes frames.
1. Physical Layer
The physical layer is in charge of the wired or wireless connections that physically connect network nodes. In addition to defining the connector, the electrical cable or wireless technology connecting the devices, it is in charge of bit rate regulation and the transmission of raw data, which is just a stream of 0s and 1s.
Advantages of the OSI Model
The OSI model benefits both network users and administrators by:
-Determining hardware and software needed to establish their network
-Recognizing and explaining the procedure used by components while communicating via a network
-Determining which network layer is the root of the problem and concentrate your efforts there
Manufacturers of networking hardware and networking software benefit from the OSI model because:
-Developing of hardware and software that can interact with products from any vendor, enabling open interoperability
-Specifying the components of the network that their products should support
-Inform users about the network tiers at which products function (i.e, only the application layer or the entire stack)
The OSI vs. TCP/IP Model
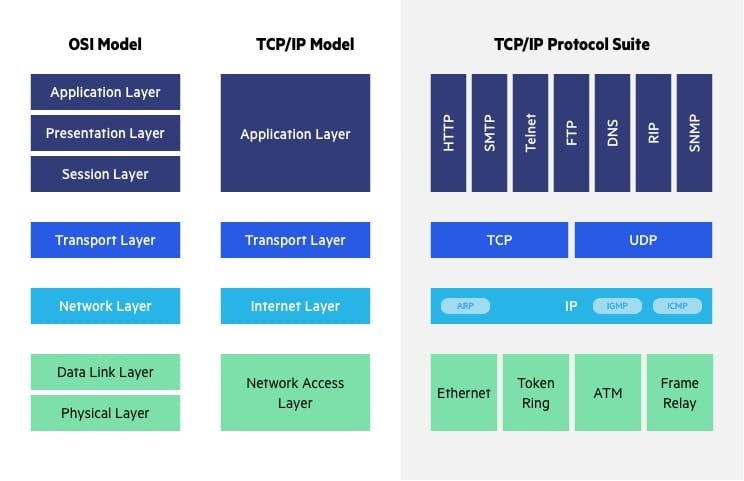
The US Department of Defense developed the Transfer Control Protocol/Internet Protocol (TCP/IP), which predates the OSI model (DoD). TCP/IP is more straightforward than other models, condensing numerous OSI levels into one:
-In TCP/IP, OSI levels 5, 6, and 7 are merged into a single application layer.
-TCP/IP combines OSI layers 1 and 2 into a single Network Access Layer, however it defers to the underlying transport layer for the functions of sequencing and acknowledgment.
Other significant variations:
-The TCP/IP functional paradigm, which is based on certain, established protocols, was created to address particular communication issues. The OSI model is a generalized, protocol-neutral framework designed to represent all types of network communication
-While most OSI basic apps do not use all seven layers, most TCP/IP applications use all seven layers. The only required levels for any type of data exchange are layers 1, 2, and 3.
Why The OSI Model Remains Relevant
-Enterprise security teams can identify and categorize physical access, where the data is located, and offer an inventory of the applications that employees use to access data and resources by knowing the many layers.
-The OSI model can also be utilized to comprehend the migration of cloud infrastructure, especially when it comes to protecting data in the cloud
-Additionally, the model has been used for a long time and is widely recognized, so networking specialists can readily comprehend the networking system’s components thanks to the uniform nomenclature.
8 Mnemonic Techniques For Remembering the OSI Model 7 Layers
From Physical to Application (Layer 1 to Layer 7):
-Please Do Not Throw Sausage Pizza Away
-Pew! Dead Ninja Turtles Smell Particularly Awful
-People Don’t Need To Stop Peeling Apples
-People Don’t Need To Sell Pringles Anymore
From Application to Physical (Layer 7 to Layer 1):
-All People Seem To Need Data Processing
-All People Search Top Notch Donut Places
-A Professor Said That Nobody Drinks Pop
-A Priest Saw Two Nuns Doing Pushups
Thank You for Reading!



