What Are Cyber Security Domains
The different contexts in which Cybersecurity approaches might be used are referred to as Cybersecurity domains. Some of the most popular cyber security domains include threat intelligence, risk assessment, threat management, and application security.
When developing a Cybersecurity policy, a company takes into account the numerous Cybersecurity facets. So you might also refer to them as realms of cyber security policy. A list of all Cybersecurity domains is provided below:
Career development
Computer operations security
Cyber forensics
ERM
Identity management
Incident response
Security architecture
Telecommunications security
User education
What are the Parts of Cyber Domain?
A person unfamiliar with cybersecurity may inquire as to what it is. The area where computer systems and networks are employed is known as a cyber domain. It is extremely complicated and constantly evolving.
To be successful, organizations must have a greater grasp of the technologies and threats that exist in the cyber world. The 5 components of the cyber realm are as follows:
The physical domain
The logical domain
The data domain
The application domain
The user domain
There are specific security threats and problems that must be managed in each area of the cyber realm. Organizations must identify and minimize the risks and problems associated with each subdomain in order to secure the cyber domain. A comprehensive plan must be developed that is referred to as a Cybersecurity policy.
The hardware and software that make up a computer system are divided into two categories: the logical domain and the physical domain. I/O devices, networking elements, CPUs, memory, storage, and other physical components of a computer system are all included in the physical domain.
The logical domain is made up of all the software that runs on a computer system, including the BIOS, operating systems, applications, and data. It outlines the access and manipulation of data. The data domain includes every piece of information kept on a computer.
The user domain is the domain that houses user information, whereas the application domain houses all the programs that are accessible on a physical device like a PC or server. PINs, passwords, security phrases and more are required to keep it secure.
The term “cyber security domain” describes the many security measures we employ to protect each type of cyber domain. Different strategies must be used for various cyber domains.
1. Frameworks & Standards
The best techniques to control Cybersecurity risk are outlined in Cybersecurity frameworks and guidelines. These provide you the option to establish controls and decide on your risk tolerance.
Many Cybersecurity frameworks and standards are blends of previous frameworks and standards.
One needs to be familiar with the various cyber security frameworks and standards in order to create a strong Cybersecurity compliance program. The following are some of the most popular cyber security frameworks and standards:
ASD (Australian Signals Directorate) Essential 8
CIS (Center for Internet Security) Controls
CISA (Cybersecurity and Infrastructure Security Agency) TSS (Transportation Systems Sector) Cybersecurity Framework
ETSI (European Telecommunications Standards Institute)
HITRUST CSF (Cybersecurity Framework)
ISA/IEC (International Society of Automation) 62443
IoTSF (Internet of Things Security Foundation) Security Compliance Framework
MITRE ATT&CK
NIST (National Institute of Technologies) CSF (Cybersecurity Framework)
NIST SP (Special Publication) 800-82 Guide to ICS (Industrial Control Systems) Security
OASIS SAML (Security Assertion Markup Language)
PCI DSS (Payment Card Industry Data Security Standard)
When creating an appropriate cybersecurity policy, a company takes into account as many cybersecurity frameworks and standards that are feasible.
2. Application Security

In order to safeguard an organization’s software and services against a wide variety of threats, application security entails the installation of numerous types of countermeasures. It simply means to protect the applications that a company creates, makes available, and utilizes.
Several steps are usually taken to prevent unauthorized access to or modification of application resources. As part of this, secure application architecture, robust data input validation, threat modeling, secure code creation, etc. are all implemented.
The numerous subdomains of application security include API security, S-SDLC, security QA, security UX, and source code scanning.
3. Risk Assessment
Risk assessment is the process of thoroughly examining the workplace to find situations, procedures, etc. that could endanger an organization’s assets, such as its people and systems. It includes:
Hazard identification
Risk analysis and risk evaluation
Risk control
In the process of assessing risk, we look for potential threats and dangers. We refer to this as danger identification. To examine and evaluate the risks related to the recognized hazards and risk factors, risk analysis and risk evaluation are performed.
The process of figuring out the best ways to reduce risks and hazards, or to control them when they can’t be eliminated, is known as risk control. Risk assessment has several subdomains, including asset inventory, penetration testing, risk monitoring services, and vulnerability scanning.
4. Enterprise Risk Management
The goal of enterprise risk management, often known as ERM, is to recognize and get ready for risks that could affect an organization’s finances, goals, and operations. It is risk management used in a business setting. Enterprise risk management includes the following subdomains:
Crisis management
Cyber insurance
Lines of defense
Risk acceptance statement
Risk appetite
Some individuals mistakenly think that ERM is a good or service, although this is untrue. It is a process instead. This could be as a result of ERM’s resemblance to ORM (object-relational mapping), CRM (customer relationship management), and ERP (enterprise resource planning).
ERM must be integrated into an organization’s work culture in order to be effective. Maintaining the reputation of the brand and ensuring long-term commercial viability are crucial.
5. Governance
An organization’s risk appetite, accountability structures, and decision-making processes can all be strategically viewed via the lens of cyber security governance. It entails making decisions to put security policies into effect.
The goal of governance is to make sure that the company can manage to make the best judgments the majority of the time and implement effective policies to reduce risk. Subdomains of governance include company written policy, executive management involvement, and rules and regulations.
6. Threat Intelligence
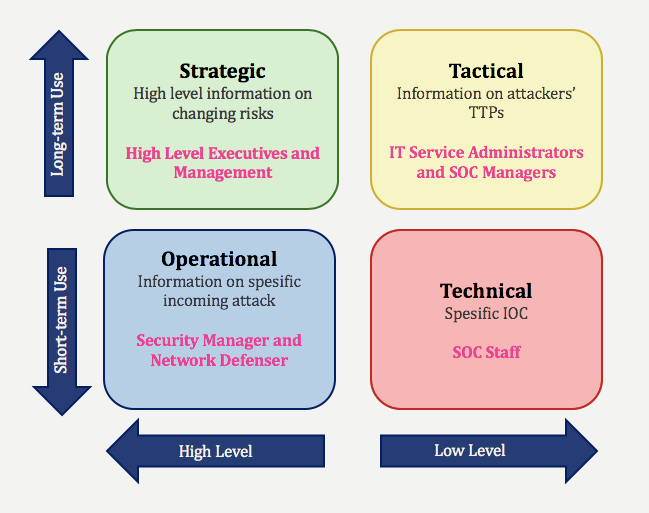
Threat intelligence, also referred to as cyber threat intelligence (CTI), is the procedure of gathering data from a broad range of sources regarding current or possible assaults against a business.
To reduce and manage Cybersecurity risks, the data gathered by CTI is examined and improved. It is employed to safeguard an organization against Cyberattacks along with other Cybersecurity solutions. External or internal threat intelligence is possible.
7. End-user Education
The major goal of end-user education is to increase employee awareness and provide them with the necessary knowledge and equipment so they can defend the company against data breaches and assaults.
Employees can educate themselves by learning about various cybersecurity-related issues, such as information security or Infosec. Cybersecurity’s information security division focuses exclusively on safeguarding data and information systems.
Confidentiality, integrity, and availability are the three areas that make up information security. The CIA trio refers to these information security sectors as a whole. End-user education includes Cybersecurity training, awareness, and tabletop exercises.
8. Security Operations
Security operations are the actions that carry out security plans. Applying resource protection strategies, disaster recovery, incident management, controlling physical security, and comprehending and assisting investigations are all covered.
In this area of cyber security, standards for investigation kinds, logging and monitoring services, and resource provision security are also included.
9. Physical Security
Protecting people, property, and tangible assets from situations and occurrences that could cause harm or loss is known as physical security. To secure the digital and physical assets of a business, various Cybersecurity teams must collaborate with each other.
This is because quickly developing technologies like the internet of things and artificial intelligence are increasing the complexity of physical security.
10. Career Development
Unbelievably, one of the cyber domains is also categorized as career growth. This is as a result of the rise in demand for knowledgeable and certified Cybersecurity personnel.
Certifications, conferences, peer groups, self-study, training, and other activities are all part of career growth in Cybersecurity. Additionally, students have a variety of topics to choose from and can enroll in courses like information security, risk analysis, or ethical hacking certification training.
11. Security Architecture

It is a unified security design that takes into account the demands and potential dangers of a particular circumstance or environment. Where and when to use security controls are also specified by security architecture. Usually, this procedure is repeatable.
The detailed security control standards and design philosophies are extensively laid forth in many sources. Security architecture’s most important characteristics are:
Benefits
Drivers
Benchmarking and good practice
Financial
Legal and regulatory
Risk management
Form
Relationships and dependencies
The critical stages of the security architecture process are architectural risk assessment, implementation, operations and monitoring, and security architecture and design.
Conclusion
A huge range of ideas, instruments, frameworks, and other things are covered by the topic of Cybersecurity. Cybersecurity has seen an unparalleled demand as a result of cyberspace’s exponential growth. Therefore, there’s no time like the present to pursue a profession in cyber security.



