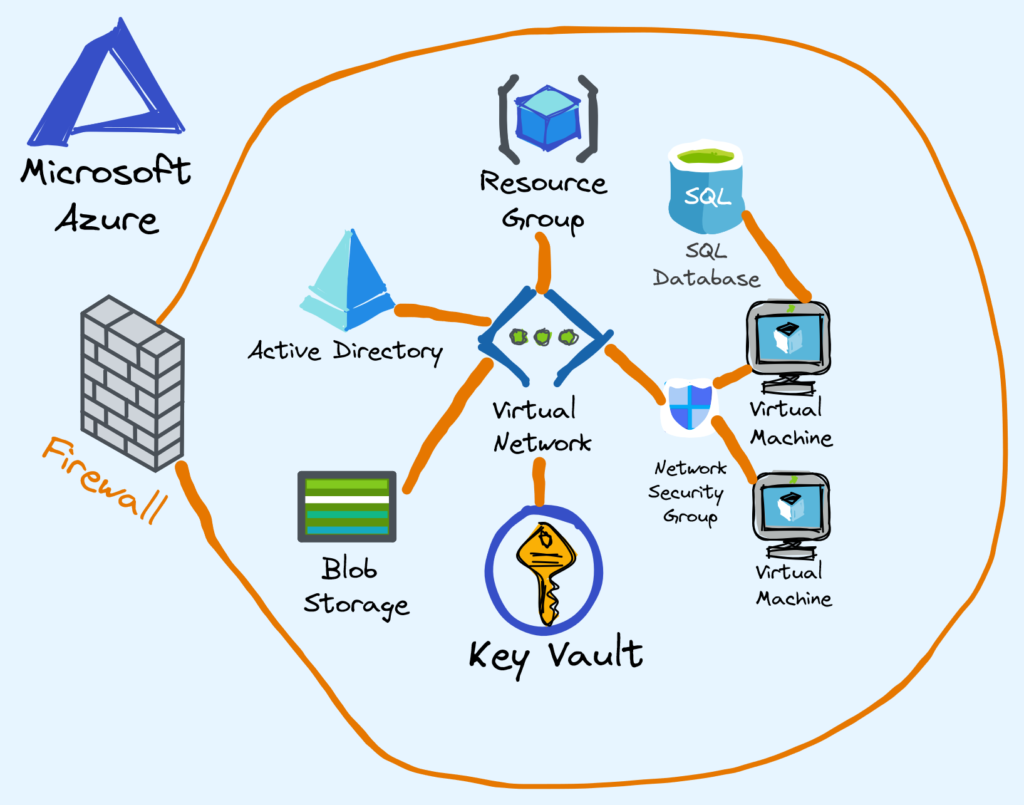
Securing a Cloud Environment
Securing a cloud environment involves a combination of technical, operational, and administrative controls. Here are some general steps that businesses can take to secure their cloud environment:
Define a security policy: Establish a security policy that outlines how you will manage and secure your cloud infrastructure. The policy should cover access controls, data protection, incident response, and other security-related issues.
Choose a secure cloud provider: Select a cloud provider that offers robust security features, compliance with industry standards, and regular security audits.
Secure network access: Use firewalls, VPNs, and other network security tools to restrict access to your cloud environment. Limit access to only those users who need it and monitor all access attempts.
Protect data: Implement encryption, access controls, and other security measures to safeguard your data. Use secure coding practices to ensure that your applications and services are not vulnerable to attacks.
Use monitoring and logging tools: Monitor your cloud environment for suspicious activity and configure logging to capture important events. Use automated alerts to notify you of potential security incidents.
Train employees: Train your employees on cloud security best practices and make sure they understand the risks associated with cloud computing. Require strong passwords and use two-factor authentication to protect user accounts.
Regularly audit and review: Regularly audit and review your cloud infrastructure to identify potential vulnerabilities and ensure compliance with security policies and regulations.
These steps will help you build a strong foundation for securing your cloud environment. However, the specific security measures you need will depend on the type of business you operate, the size of your organization, and the level of risk you are willing to accept. It’s important to work with a security professional to develop a tailored security plan that meets your specific needs.
NIST As A Guide

The National Institute of Standards and Technology (NIST) Special Publication 800-61 outlines the Computer Security Incident Handling Guide, which includes a set of steps for handling cyber security incidents.
Preparation: Establish policies, procedures, and a plan for incident response. Identify and prioritize critical assets and personnel, and train and prepare them for potential incidents.
Detection and Analysis: Monitor and detect potential incidents. Analyze the incident to determine its scope and impact.
Containment, Eradication, and Recovery: Contain the incident to prevent further damage. Eradicate the cause of the incident and restore systems to normal operation.
Post-Incident Activity: Review the incident and the response to identify areas for improvement. Update policies and procedures based on lessons learned.
Reporting: Report the incident to appropriate internal and external parties, such as law enforcement, regulatory agencies, and affected parties.
Remediation: Take steps to prevent similar incidents from occurring in the future. Implement controls to reduce the likelihood and impact of future incidents.
These steps provide a framework for organizations to effectively respond to cyber security incidents and minimize the impact on their operations.
The Benefits of Azure Security
Microsoft Azure provides a comprehensive set of security features and services to help businesses protect their cloud infrastructure, applications, and data. These security measures can be grouped into several categories, including network security, identity and access management, data protection, and threat detection and response.
One of the key benefits of Azure’s security offerings is that they are designed to provide end-to-end security for cloud workloads, from the network layer all the way up to the application layer. This means that businesses can rely on Azure to secure their entire cloud environment, rather than having to manage security measures separately for different components.
Azure also offers advanced security capabilities, such as machine learning-based threat detection and response, encryption for data at rest and in transit, and secure connectivity options for hybrid cloud environments. These capabilities can help businesses improve their overall security posture and reduce the risk of data breaches or other cyber attacks.
In addition to these technical security measures, Azure also provides compliance certifications and tools to help businesses meet regulatory requirements for data security and privacy. This can be particularly beneficial for businesses in regulated industries or those that deal with sensitive customer data.
Overall, Microsoft Azure’s comprehensive security offerings can provide businesses with the peace of mind that their cloud infrastructure, applications, and data are well-protected from cyber threats.
Azure Security Preparation

Azure Log Analytics workspace is a centralized solution that enables you to collect, analyze, and visualize logs from various Azure and non-Azure resources. It can help with incident detection and response by providing the following benefits:
Centralized Log Collection: Log Analytics workspace can collect logs from various Azure and non-Azure resources, including virtual machines, containers, and applications. This centralized approach allows for quick identification of issues that may occur in your environment.
Advanced Analytics: With Log Analytics workspace, you can perform advanced analytics on the collected logs, including the use of machine learning algorithms. This enables you to identify patterns and anomalies that may indicate potential security threats or issues that require attention.
Real-time Alerts: Log Analytics workspace can be configured to send alerts in real-time when specific events or conditions are met. This enables you to quickly respond to security incidents and other critical events.
Custom Dashboards: Log Analytics workspace allows you to create custom dashboards that can display data from various sources in a single view. This can help you to quickly identify trends and issues in your environment.
Integration with Other Azure Services: Log Analytics workspace can be integrated with other Azure services such as Azure Security Center, Azure Sentinel, and Azure Automation. This enables you to automate incident response and remediation tasks.
Custom Logging
In Azure, custom logging refers to the ability to collect and analyze logs generated by your applications or infrastructure in a centralized and efficient way.
Azure provides various logging options, such as Azure Monitor, Azure Log Analytics, and Azure Application Insights, that enable you to collect, analyze, and act on log data from different sources. These services allow you to collect logs from Azure resources, such as virtual machines, databases, and storage accounts, as well as from custom applications running on-premises or in the cloud.
To set up custom logging in Azure, you typically need to follow these steps:
Determine what log data you want to collect: This could include system logs, application logs, security logs, and other types of data.
Choose a logging service: Azure offers several logging services, and each has its strengths and weaknesses. For example, Azure Monitor is great for collecting and analyzing infrastructure logs, while Application Insights is ideal for monitoring custom application metrics and telemetry.
Configure logging sources: Once you’ve chosen a logging service, you need to configure your applications or infrastructure to send log data to that service. This usually involves installing an agent or collector, configuring logging settings, and ensuring that the logs are properly formatted.
Analyze log data: With log data flowing into your chosen logging service, you can then analyze it to identify issues, troubleshoot problems, or gain insights into how your applications and infrastructure are performing.
Overall, custom logging in Azure is a powerful tool for monitoring and managing your cloud-based applications and infrastructure, helping you to ensure that your systems are performing optimally and securely.
You can find Microsoft’s official documentation for Azure Log Monitor here.
This documentation covers everything you need to know about Azure Log Monitor, including how to set it up, how to use it to monitor logs from Azure resources and custom applications, and how to query and analyze log data using Azure Monitor Logs.
The documentation is organized into different sections, each covering a different aspect of Azure Log Monitor. Some of the key topics covered in the documentation include:
Introduction to Azure Log Monitor: This section provides an overview of Azure Log Monitor and its key features.
Getting started with Azure Log Monitor: This section covers the steps involved in setting up Azure Log Monitor and configuring it to collect logs from Azure resources and custom applications.
Analyzing log data with Azure Monitor Logs: This section covers how to use Azure Monitor Logs to query and analyze log data, including using the Kusto Query Language (KQL) to create queries and filters.
Using Azure Log Monitor with other Azure services: This section covers how to integrate Azure Log Monitor with other Azure services, such as Azure Event Hubs, Azure Functions, and Azure Stream Analytics.
Best practices for using Azure Log Monitor: This section provides tips and best practices for using Azure Log Monitor effectively, including how to optimize performance, manage costs, and troubleshoot issues.
In summary, Log Analytics workspace and custom logging provides a powerful tool set for incident detection and response in Microsoft Azure. It enables you to centralize log collection, perform advanced analytics, receive real-time alerts, create custom dashboards, and integrate with other Azure services to automate incident response tasks.
Azure Sentinel and It's Business Benefits and Capabilities

Azure Sentinel is a cloud-native Security Information and Event Management (SIEM) service provided by Microsoft Azure. It is designed to provide intelligent security analytics and threat intelligence across the entire enterprise, helping businesses to detect, prevent, and respond to security threats in real-time.
Azure Sentinel uses artificial intelligence and machine learning to analyze large volumes of data from various sources, such as endpoints, cloud applications, and network devices, to detect potential threats and provide actionable insights to security teams. It also integrates with other Microsoft security solutions, such as Microsoft Defender for Endpoint and Microsoft Cloud App Security, to provide a comprehensive security solution.
Some of the key benefits of Azure Sentinel for businesses include:
Centralized security management: Azure Sentinel provides a centralized location for security management, allowing security teams to monitor security alerts and incidents across all environments, including on-premises and cloud-based infrastructure.
Real-time threat detection: Azure Sentinel uses advanced analytics to detect potential threats in real-time, providing security teams with the ability to respond quickly to security incidents.
Customizable dashboards: Azure Sentinel provides customizable dashboards that allow security teams to view critical security information in real-time, making it easier to identify and respond to security threats.
Scalability: Azure Sentinel is a cloud-native service that can easily scale to meet the needs of any size organization.
Reduced costs: Azure Sentinel can help businesses to reduce their security costs by providing a cloud-based solution that eliminates the need for on-premises hardware and software.
Azure Sentinel provides businesses with an intelligent and scalable cloud-based solution for managing their security operations and protecting their data and assets.
Microsoft Defender for Cloud Security Integration

Microsoft Defender for Cloud is a cloud-native security solution designed to help businesses protect their cloud infrastructure and applications. It provides advanced threat protection for workloads running on Azure, AWS, and other cloud environments, as well as for on-premises servers.
When integrated with Azure Sentinel, Microsoft Defender for Cloud can provide a more comprehensive security solution. The integration allows Azure Sentinel to receive alerts and threat intelligence from Defender for Cloud, which can be used to enhance the detection and response capabilities of Azure Sentinel.
For example, Defender for Cloud can detect suspicious activities such as brute-force attacks or data exfiltration attempts on a company’s cloud infrastructure, and then send an alert to Azure Sentinel. Azure Sentinel can then correlate this alert with other security events across the environment to determine whether it is part of a larger attack campaign. If necessary, Azure Sentinel can also trigger automated responses, such as quarantining a compromised system or blocking a malicious IP address.
Defender for Cloud can also integrate with other popular cloud platforms such as Amazon AWS and Google Cloud.

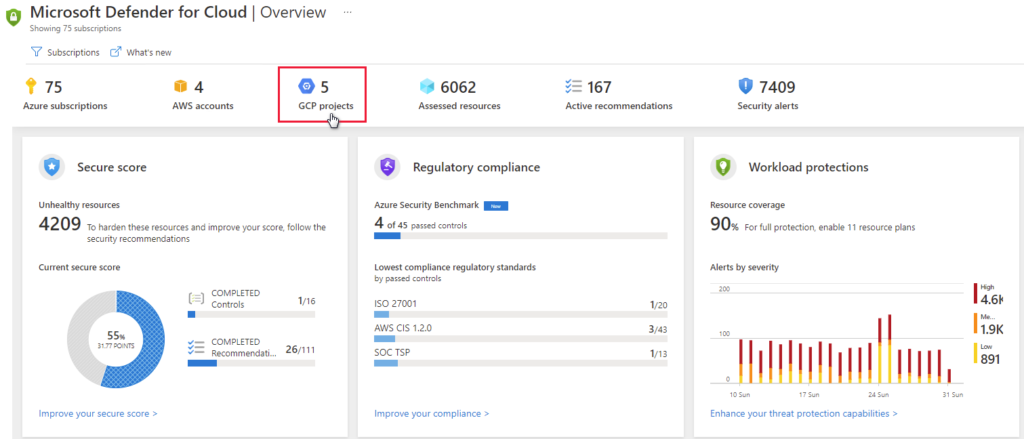
The benefits of Sentinel and Defender for Cloud integration are:
-Improved threat detection and response
-Simplified Security Management
-Compliance and Governance
-Cost-Effective Security
-Scalable Security
As one can see, securing a cloud environment is the most important step a business can take when in the cloud. Integrating Microsoft Defender for Cloud with Azure Sentinel can help businesses gain a better understanding of their security posture, identify threats faster, and respond more effectively to security incidents.
Video Demonstration of Sentinel in Action
Thank You for Looking!
Everything I learned to write this post I learned taking Josh Madakor’s Cyber Security course on Leveld Careers. You can check it out here.
To see Josh Madakor’s Youtube Channel visit my favorite Youtubers Page.




